Top Security Equipment Suppliers for Advanced Custom Security Solutions
Discovering the Role of Accessibility Control Systems in Enhancing Safety Tools Efficiency and Efficiency
Accessibility control systems are significantly identified as vital parts in the landscape of protection management, offering a structured approach to regulate accessibility to delicate locations and info. Their capability to incorporate with different safety innovations, such as monitoring video cameras and alarm systems, substantially enhances the total efficiency and effectiveness of security procedures.
Comprehending Gain Access To Control Solution
Access control systems play a crucial role in making certain the safety of numerous settings, from business offices to delicate government centers. These systems control that can go into or exit an assigned area, therefore securing properties and delicate information. The essential components of accessibility control systems include authentication, identification, and permission procedures.
Identification entails verifying a person's identification, normally with credentials such as crucial cards, biometric data, or passwords. Once identified, authentication validates the individual's right to accessibility, typically with multi-factor verification methods to improve security. Finally, consent figures out the level of gain access to provided, allowing for separated approvals based on roles within the organization.
Gain access to control systems can be classified right into two main types: sensible and physical. Physical accessibility control pertains to concrete areas, while sensible accessibility control regulates electronic details systems. Both kinds function synergistically to provide extensive safety and security services.
Integration With Protection Technologies
The assimilation of gain access to control systems with other safety and security technologies is important for creating a holistic protection atmosphere. By integrating access control with video clip monitoring, invasion detection, and security system, organizations can enhance their total safety stance. This interconnected structure enables for real-time surveillance and fast reaction to protection cases, boosting situational understanding and functional effectiveness.
For example, incorporating access control with video clip surveillance makes it possible for safety personnel to confirm access events visually, ensuring that only licensed individuals are given access. When accessibility control systems are connected to alarm system systems, any kind of unapproved access efforts can trigger instant informs, prompting quick action.
Additionally, the assimilation of access control with cybersecurity procedures is significantly vital in shielding delicate data and physical possessions. By straightening physical protection procedures with IT security systems, organizations can guarantee that both electronic and physical gain access to factors are monitored and controlled efficiently.
Benefits of Improved Safety Workflow

Furthermore, improved safety and security operations promote real-time surveillance and occurrence action. With integrated systems that encompass security electronic cameras, alarm systems, and gain access to controls, safety and security groups can promptly determine and attend to prospective threats. This aggressive technique enables for prompt treatments, decreasing the probability of safety and security violations and prospective losses.
Additionally, reliable safety operations add to a culture of safety within the company. Employees are most likely to feel even more safe when they understand that durable steps remain in visit our website location, leading to boosted morale and performance. Additionally, using data analytics from access control systems allows companies to evaluate security patterns, enhance policies, and allot resources successfully.
Challenges and Considerations
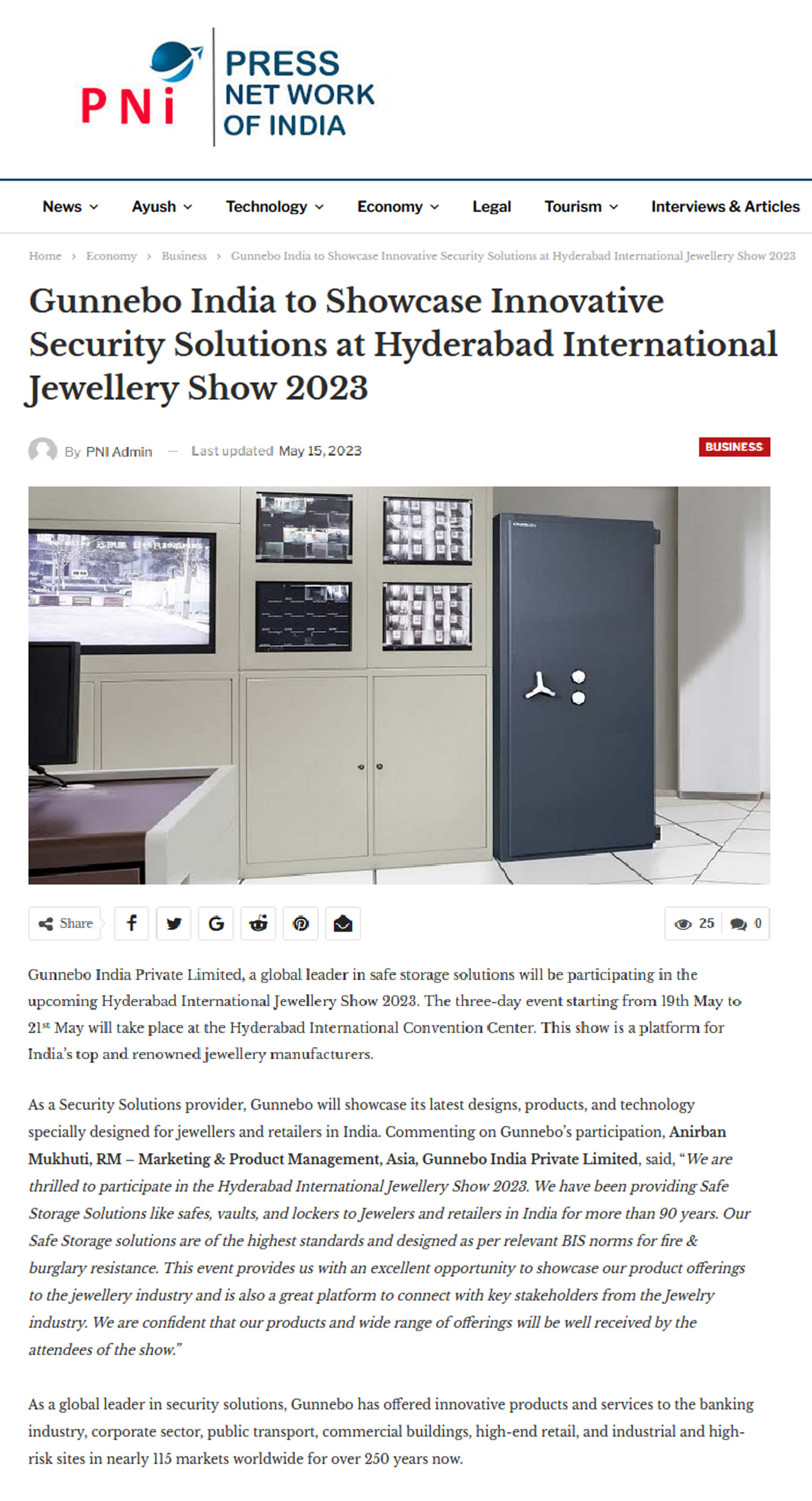
Additionally, organizations need to resolve the potential for data breaches. Gain access to control systems usually handle delicate information, and any susceptabilities can expose this data to unauthorized gain access to. security equipment suppliers. Guaranteeing robust cybersecurity steps is important to shield against such risks
User training is another vital consideration. Workers should understand exactly how to utilize gain access to control systems efficiently, as incorrect usage can lead to security voids. Organizations have to stabilize safety and security with user ease; extremely restrictive access can hinder performance and lead to workarounds that jeopardize security methods.
Conformity with regulatory and lawful demands is also extremely important. Organizations needs to guarantee that their accessibility control systems satisfy sector criteria and local regulations, which can vary significantly. Ultimately, the ongoing upkeep and management of these systems call for specialized resources, making it vital for organizations to allot suitable spending plans and personnel to make certain long-term performance and efficiency.

Future Patterns in Accessibility Control
Anticipating the future of gain access to control reveals a landscape progressively formed by technical advancements and progressing protection needs. One considerable pattern is the integration of expert system (AI) and equipment learning, which improve decision-making abilities and automate danger discovery. These innovations enable real-time analysis of access patterns, allowing more flexible and receptive protection actions.
Biometric verification is also getting traction, with developments in finger print, face acknowledgment, and iris scanning technologies offering enhanced security and customer convenience. address As these systems become more sophisticated and budget friendly, their adoption throughout various industries is expected to rise.
An additional arising pattern is the shift towards cloud-based access control systems. These services offer scalability, remote administration, and centralized information storage space, enabling organizations to enhance and enhance operations efficiency.
In Addition, the Web of Things (IoT) is set to change gain access to control by allowing interconnected devices to connect and share data, thereby boosting situational understanding and safety and security responsiveness.
Conclusion
In verdict, access control systems substantially boost the effectiveness and effectiveness of safety tools by facilitating precise identification, authentication, and consent procedures. While considerations and difficulties exist, the continuous advancement of accessibility control technologies promises to further enhance safety procedures.
Accessibility control systems are increasingly identified as essential components in the landscape of safety and security administration, supplying a structured technique to control access to sensitive locations and details. Physical accessibility control pertains to substantial areas, while sensible accessibility control regulates digital info systems.The assimilation of accessibility control systems with various other safety innovations is vital for producing an alternative safety and security environment. Access control systems frequently handle sensitive details, and any vulnerabilities could expose useful content this information to unapproved accessibility. Organizations should balance protection with individual benefit; overly limiting gain access to can hinder performance and lead to workarounds that jeopardize safety and security protocols.